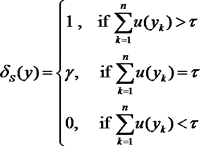Overview
- Possibility of Denial of Service (DoS) attacks in the MAC layer
- MAC and routing layers interact
- Current protocols offer insufficient cross-layer interaction
- Possible to cause an attack by manipulating traffic in the MAC layer and propagate attack to the routing layer
- Need for additional interaction between MAC and routing:
- MAC needs to pass information to routing in case of congestion
- Routing decides on new routes that are not affected by congestion;
- IDS makes sure the new routes don’t contain malicious nodes
Goal
Detect the intrusion, minimizing detection time tD and the number of false alarms, while maximizing the probability of detection PD
MAC Layer Issues
Solve the following problems:
- Best strategy for detection of misbehaving nodes
- How long a malicious node can stay malicious? Will it eventually collide with normal node?
- What is the best strategy to stay undetected?
- Can colluding nodes be successfully detected?
MAC Issues – Node Misbehavior
- Most communication protocols assume honest participants.
- Node misbehavior can occur at different layers, e.g.:
- MAC: Violate Back-off procedure to obtain better throughput
- Routing: Do not forward packets on behalf of other nodes in order to save battery
- Transport: Change congestion avoidance parameters to obtain better throughput in TC
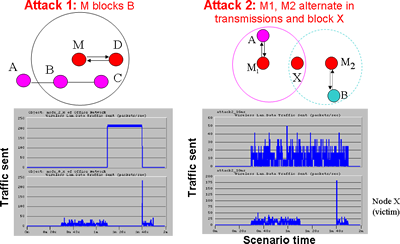
Detection of Greedy�Behavior In 802.11
- Fewer retransmissions than any other node
- Violating DIFS or SIFS periods
- Setting large NAV values for other contending nodes
- Deauthenticate other contending nodes
- Violate the Back-off Mechanism
Results
Non-parametric Test
A non-parametric test is used since we do not know a priori the distribution the misbehaving nodes will use to access the channel.
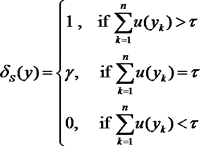
Detection results

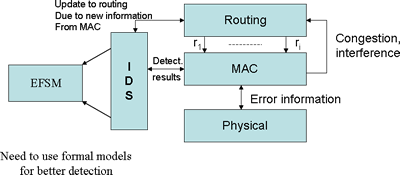
Why cross-layer?
- No cross-layer interaction
- Routing can select between several routes
- Has no information about congestion or malicious nodes
- It selects a congested route – MAC cannot forward traffic or
- It selects route that includes malicious node(s)
- After timeout it selects a new route in vicinity of the existing route – cannot forward packets due to the same reason
- With cross-layer interaction
- Routing forwards possible route choices to MAC
- MAC decides on possible routes using congestion and IDS information
- MAC returns the result to the routing
Cross-Layer Scheme
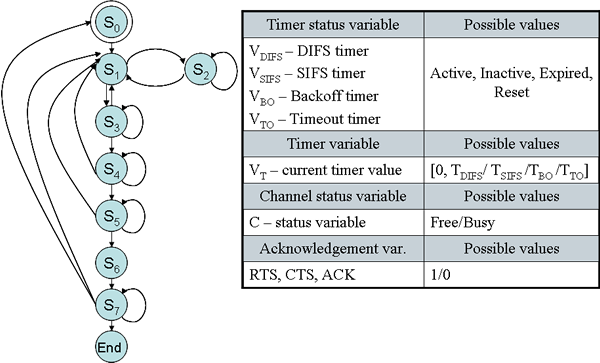
Formal Model